Cybersecurity
Don't worry about digital threats - fight them!
Our solutions help you secure your networks, servers, applications, and sensitive data from cyber attacks. Thanks to our expertise in both hardware and software, we provide a comprehensive perspective of IT security. From the analysis of potential threats and the current state of your infrastructure, through the design of resilient and robust solutions, to precise technological procedures and implementation, suitable for even the most sensitive data.
We also deal with the complete outsourcing of IT and cybersecurity operations for companies, offices and organizations.


Security levels of the company or organization
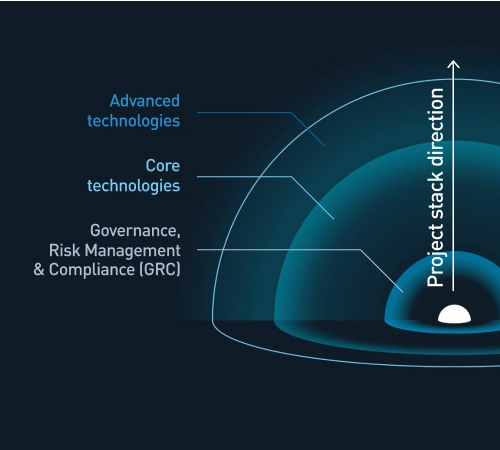
Governance, Risk Management and Compliance (GRC)
Order, compliance with procedures and legislation, and vulnerability management represent the very foundation without which information security cannot be achieved. We will make sure that these foundations are impenetrable, assist you in implementing them within your organisation and effectively integrate them with the latest technologies. Examples of such processes include the following:
Core technologies
Core technologies such as firewalls, VPN concentrators, and network anomaly detection devices are the backbone of our technology projects. We have a certain number of qualified experts, which is why we can offer customers a tailor-made and at the same time vendor neutral solution. Examples of such solutions include the following:
Advanced technologies
In today's fast-paced world, you cannot settle for passive protection. Digital threats are evolving every day, and if you want to defend yourself, you need to proactively counter them. Innovate, analyze and always be one step ahead.
Regular vulnerability testing, monitoring of users and their behavior, but also the involvement of artificial intelligence in the defence of your infrastructure will help you react flexibly to new and unexpected threats. Such technologies and processes include, for example, the following:


Security Operation Center
Do you need to take care of the security of your ICT infrastructure, but you do not want or do not have the resources and capacity to build an in-house team?
Use your resources more efficiently and outsource security to our SOC - Security Operations Centres. We respond effectively and quickly to potential threats while acting as a focal point for cooperation in monitoring, evaluating and defending against attacks.
Get in touch with our experts for more information.
Implementation procedure
-
GRC requirements
-
Analysis of the current state
-
Solution design
-
Implementation
-
Pilot operation
-
Post-implementation support
In order to prepare an impenetrable infrastructure, it is necessary to first analyze the risks we face and at the same time ensure that the proposed procedures are in accordance with the applicable legislation. Subsequently, we can answer the key questions of why and how to comprehensively and systematically solve the issue of cyber security.
This will help us determine all the prerequisites that the final system should meet, so that we can prepare first a rough design (selection of technologies, concepts, etc.) and later a more detailed design (adaptation and connection to the local infrastructure).
After the management processes (risk management, incident resolution, etc.) are defined in accordance with the applicable legislation, we can proceed to the introduction of the individual phases of the implementation process and finally to the pilot operation together with the submission of complete documentation. In case of any post-implementation problems, our technical support is still available for you.
Our service portfolio
-
Penetration testing
AdvancedOur operational team will actively try to attack your system. By doing so, our specialists can check the treatment of known errors, search for potentially dangerous information and test the vulnerabilities that hackers may exploit in your system (configuration errors, old unused tools, user errors, etc.).
The output of the penetration test is a detailed report on the aforementioned vulnerabilities. We will also provide you with procedures on how to remove such vulnerabilities and suggestions on how to prevent them in the future. -
Threat hunting
AdvancedThreat hunting is the process of actively searching for previously undetected, unknown or unremoved cyber threats and risks on your network. It helps to prevent security threats, but also to reduce the time from intrusion to detection, thus reducing the damage caused by attackers.
-
EDR, XDR
AdvancedEDR - endpoint detection and response - is a technology that continuously monitors an endpoint (a device connected to a network, such as a computer or printer) in order to mitigate cyber threats. It is used to detect malicious or suspicious activity on a computer and respond to this activity. EDR intercepts the threat at the endpoint and helps eliminate it before it spreads to the network.
XDR - extended detection and response - is a tool that offers security by integrating security products and data into simplified solutions. XDR collects data to provide an overview of potential advanced threats as well as of their context in the system. Threats can then be analysed, prioritised, searched for and removed to prevent data loss and security breaches.
-
AI Systems
AdvancedThe goal of artificial intelligence (AI) is to create technologies that can think, learn and adapt like humans. This technology works independently, is able to perceive its environment and take such measures to maximize the chance of successfully completing the task. It can also interpret and analyze data, learning and adapting to your system.
-
Vulnerability monitoring of IT infrastructure
CorePeriodic scanning and auditing of infrastructure vulnerabilities provides us with valuable information about the status of the systems and their current level of security, which in turn gives us the opportunity to improve the level of security. Thanks to the early detection of vulnerabilities, we can achieve a higher overall security level and thus reduce the risk. The result is a systematic report of the scans and suggestions for corrective action.
-
Network security
CoreToday, information and communication technologies form the backbone of every organization. In a world full of cyber threats - malware, ransomware and DDoS attacks - this critical infrastructure is under constant threat and securing it must be a priority for every organization.
We will make your network a robust and secure infrastructure. We will design a structure with separate network segments, monitored data flows, access trust management and application-level security thanks to firewalls, IPS, Proxy, etc.
-
Firewalls
CoreFirewalls represent the first line of defence in the field of network security. A firewall is a network security device that blocks or allows network traffic based on preset or dynamic rules and policies. It protects networks and computers from unauthorized interference.
-
VPN
CoreA Virtual Private Network creates an encrypted communication tunnel between your device and typically an organization's network. Subsequent communication over the Internet takes place via an encrypted channel, so your connection to the company network remains secure. In this way, the risk of breaching the confidentiality of your communication is minimized.
-
Multifactor authentication
CoreIt provides convenient, yet highly manageable access to the systems of any organization. In today's world of cloud solutions, remote access and massive use of mobile devices, user authentication, security and verification are top priorities. Multi-factor authentication enables secure access to internal networks, protects users' personal information, provides centralised control of data and helps reduce costs for the organisation.
-
SIEM
CoreSecurity Information and Event Management (SIEM) provides relevant security information from the IT infrastructure in real time and evaluates risk events. It provides organisations with an overview of the activity within their network, so that they can respond quickly to potential cyberattacks and meet compliance requirements.
-
Risk management
GRCHaving perfect cybersecurity is impossible. Threats are constantly evolving and resources are always limited. That is why it is important to know what level of risk is acceptable and which are the areas where security issues are most pressing. We shall provide you with management and a set of rules that make it easy to prioritise what is important, while preventing the security of any area from falling below an acceptable level.
-
Analysis and response to security incidents
GRCThe solution ensures that your assets are regularly checked for potential attackers. Even if you regularly identify and remediate vulnerabilities and regularly train your staff and specialists, assets can still be compromised. If a security incident does occur, you need to be able to react quickly and correctly. You need to carry out a thorough analysis, determine the potential extent of the damage, identify the perpetrator, collect evidence and provide a remedy.
-
Compliance with legislation
GRCSafety legislation sets standards on how to create and maintain a safe environment. It is necessary to set up the operations in such a way that they comply with the applicable legislation.
-
GDPR – General Data Protection Regulation
GRCDo you process the personal data of your employees, customers or suppliers?
Make sure that you are processing them in accordance with GDPR.We will help you with the correct implementation at all points of contact, take care of customer data security and set up processes that will ensure that you are always in compliance with the applicable legislation.
-
Information security management
GRCThis is a service that consists of aligning the level of information security in your organisation with your activities, regulatory requirements and market expectations. It represents a basic approach to creating an environment that will provide the necessary protection of information from threats.
Cybersecurity implementation case studies
Our team has extensive experience in providing cybersecurity for companies of various sizes. See how we handle both simple and challenging situations in case studies.
The newly created SOC center makes full use of elements of behavioral analysis and elements of machine learning. It also uses the global cybersecurity intelligence database to evaluate individual criteria.
Cooperation on the creation of a SOC environment at the customer together with specific procedures based on MITER how to react to individual types of reports.
Analysis of risks from the point of view of cyber security based on ISO frameworks: 27001 or 27005. Their subsequent management, risk management and communication process.
As part of the deployment of security technologies, we also deployed advanced network and behavioral analysis technologies in this project.
One of our most complex projects in the field of cyber security included a complete supply of hardware for the construction of a private cloud environment. The deployment of hardware technologies and the detailed configuration of security elements such as SIEM, VPN, Flowmon, and DDoS protection were a matter of course. Subsequent Agreement on the level of services provided. Currently, the cloud itself serves hundreds of projects and thousands of tenant VMs.
An important element of this project was its complexity in terms of the necessity of legal requirements such as: Cyber Security Act, or GDPR.
We performed a comprehensive penetration test of a web application for our important client. The process itself also included participation in fixing vulnerabilities and a subsequent re-test.


